Fortify Your Risk Management with C4 Intelligence Platform™
Turn noisy security data into clear signals.
Capture, Collect, Correlate, & Clarify
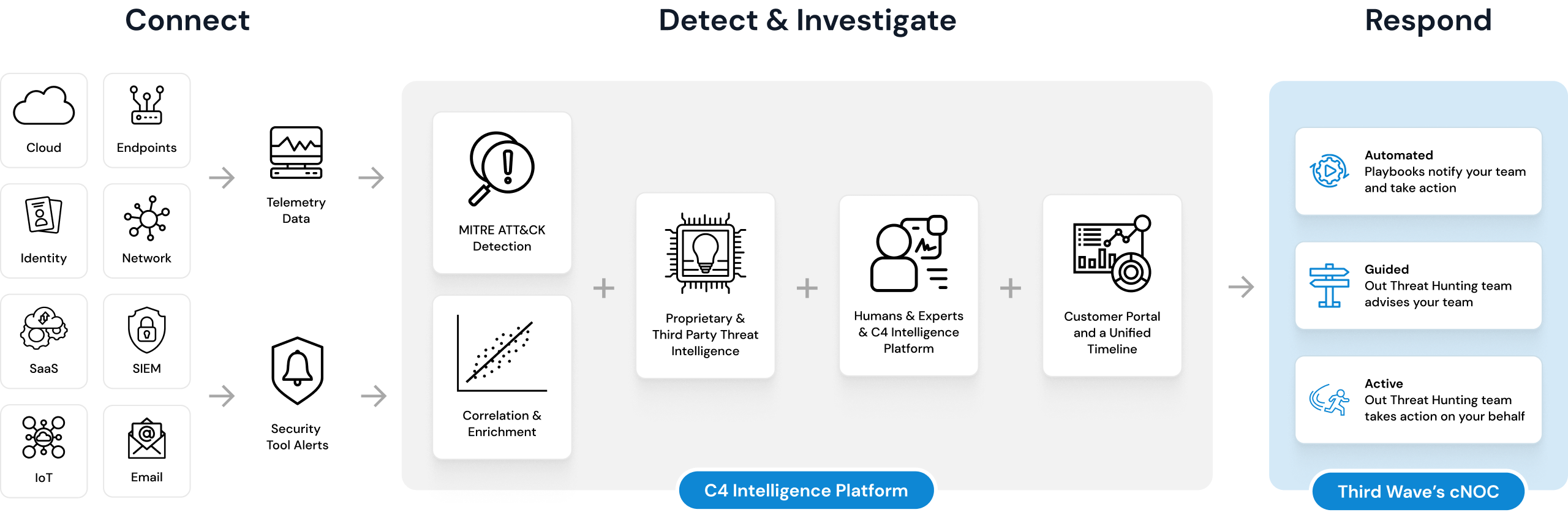
Integrations
Capture & Connect









over 300 current integrations
Third Wave's MDR
Detect & Investigate
Leverage advanced threat detection and expert analysis to safeguard your digital assets with ThirdWave.
Threat Intelligence
Gain insights with our proprietary and third-party threat intelligence.
Human Experts
Tap into the expertise of our analysts and the power of our C4 intelligence platform.
Unified Timeline
Track and manage incidents seamlessly with our unified timeline portal.
Cyber Network Operations Center (cNOC)
Respond
Third Wave’s cNOC, powered by the C4 Intelligence Platform, mitigates threats and ensures rapid response resulting in minimal to no downtime.
Automated
Our AI decision engine reduces time ot verdict and takes decisive action to neutralize threats.
Guided
Third Wave’s security experts advise on the best course of action.
Active
Trust Third Wave to take proactive measures and act on your behalf to eliminate threats.
Use cases
Greater visibility & control
For Executives
Strategically align your security landscape with business objectives to protect critical data assets.
For Information Security Managers
Streamline decision-making, optimizing security planning and operations.
For Security Analysts & IT Practitioners
Efficient threat detection, incident management, and operational support.
Ready to Take the Next Step?
The simplification of your Cybersecurity challenges begins here