Fortify Your Risk Management with C4 Intelligence Platform™
Unleash the Power of Advanced Data Analytics
C4 - Capture, Collect, Correlate, and Clarify
C4 Intelligence Platform is the groundbreaking tool designed to transform vast amounts of data into actionable insights. With our innovative four-step process – Capture, Collect, Correlate, and Clarify – we empower your organization to make smarter, faster decisions.
Capture
Seamlessly adapt and integrate diverse data sources.
Collect
Efficiently store and manage data for enhanced security and policy formulation.
Correlate
Align your operations with key compliance standards like HIPAA, ISO, PCI-DSS, and more.
Clarify
Promote company-wide awareness with digitized, easy-to-understand reports and communications.
C4 is your versatile ally in today’s rapidly evolving threat landscape.
Whether it’s security, application monitoring, or cloud cost management, C4 adapts to your needs. It surpasses traditional tools by integrating threat intelligence, robust reporting, real-time alerts, and rapid data processing across all sources, all through a single operations console.

Network
The C4 platform is at the core of our Managed Network Services capabilities. C4 provides visibility to all the necessary systems to properly manage our customer’s network infrastructure and related components.
Compliance
C4 capabilities extend beyond cybersecurity threat management with the addition of compliance monitoring and reporting. C4 creates the ability to connect threats and incidents with audit information and use case investigations that go beyond incident attribution.
Cybersecurity
C4 is designed as an open Extended Detection and Response platform integrating event and telemetry data from multiple technologies. C4 provides real-time threat detection and extends your defense with endpoint detection, advanced threat hunting, and proactive mitigation.
Risk
C4 offers a holistic approach to risk management.C4 provides the foundation to assess risk using industry standards by considering asset vulnerabilities, with a comprehensive risk profile that encompasses potential exploitation and available mitigations.
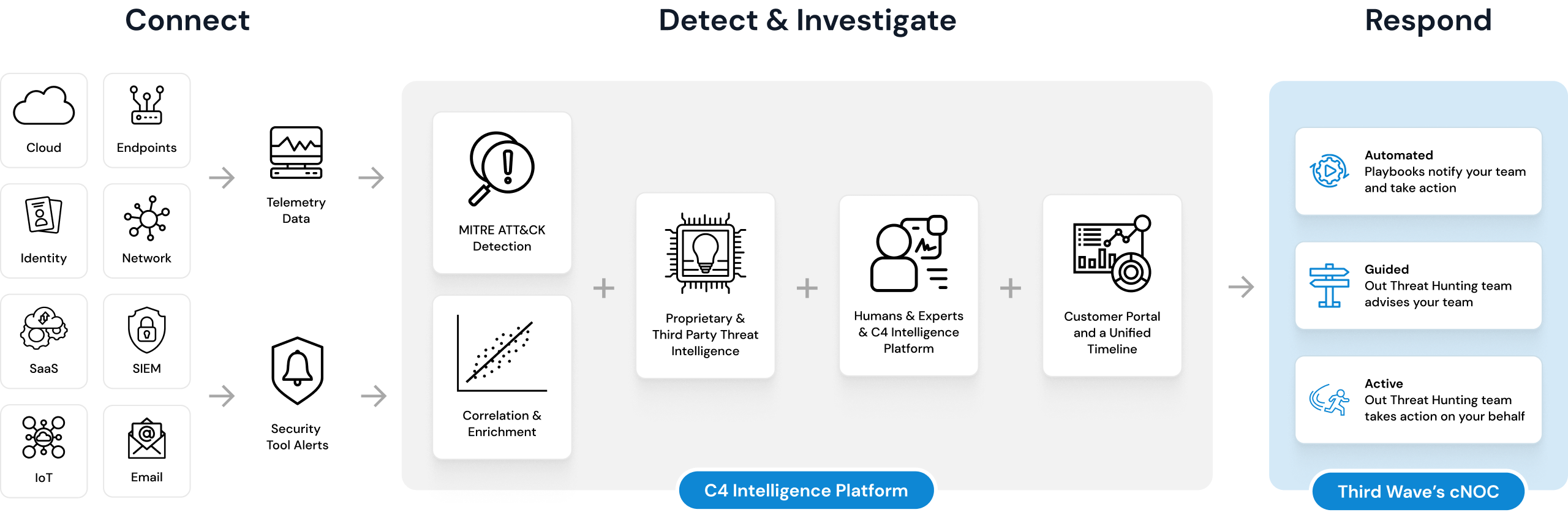
Use cases
Greater visibility and control
For Executives
Strategically align your security landscape with business objectives to protect critical data assets.
For Information Security Managers
Streamline decision-making with a dynamic operational dashboard, optimizing security planning and operations.
For Security Analysts & IT Practitioners
Utilize our advanced analytical toolkit for efficient threat detection, incident management, and operational support.
Ready to Take the Next Step?
The simplification of your IT and Cybersecurity challenges begins here